AZ900 – Azure Security Features
In the previous post of this AZ900 series, we looked at Microsoft's various networking security options within the Azure platform. I will now discuss other security features Microsoft offers.
Azure Security Center
We will look at Azure Security Center first. Azure Security Center monitors all your services to strengthen your security posture both in Azure and within your on-premises infrastructure, which will help prevent and respond to potential or active security threats.
Security Center will provide recommendations based on your current configuration and resources. It can also apply security settings to new resources on creation. It continuously monitors all resources identifying new potential vulnerabilities and alerting you and your team to issues.
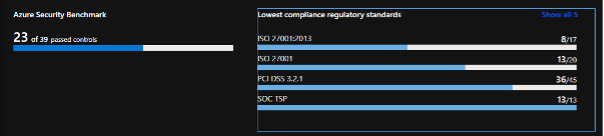
Security Center can display a range of metrics and reports, including Policy & Compliance, Resource Hygiene and Secure Score.
Policy & Compliance
Azure offers a range of reports to ensure compliance with various regulatory standards or custom compliance, e.g. ISO 27001 or PCI DSS
Secure Score and Resource Health
Microsoft Azure provides a Secure Score which is a metric that can measure the security posture of your Azure subscriptions, the lower your score means the higher the identified risk. Azure also provides an overview of the resource health, providing a view of high, medium or low-security issues and the affected resources.
Azure Sentinel
Microsoft also offers its own cloud-based Security Information and Event Management (SIEM) system called Azure Sentinel. This system can provide security and threat analytics by allowing data to be collected and applied to AI models to detect threats.
Azure Sentinel supports a wide variety of data sources for analysis. You can connect to Microsoft solutions (e.g. Microsoft 365, Azure Active Directory), other services also provide connectors to Sentinel (e.g. Citrix Security Analytics, Sophos XG Firewall), Sentinel also supports other standard formats (e.g. REST APIs, Common Event Format)
Microsoft provides a range of Built-in analytics; these are based on common attack vectors and can be used to alert suspicious activity within your environment. You can also create custom rules for specific requirements.
Once Azure Sentinel detects suspicious activity, users can be alerted to start investigations using the tools provided, like the investigation graph shown below.
Key Vault
You can use Azure Security Center and Azure Sentinel to identify and mitigate threats. Microsoft also offers services to protect application secrets and encryption keys. Azure Key Vault can protect your secrets, encryption keys, and SSL certificates.
Azure Key Vault provides a centralized store for all application secrets, which other services can use via secret references. It also provides a service with proper authentication and authorization built-in that allows access control and monitoring to ensure proper control of application secrets.
Azure Dedicated Hosts
Alongside Azure Security Center and Azure Key Vault, Microsoft also offers Azure Dedicated Hosts to ensure regulatory compliance when there is a requirement to be the only user of the underlying hardware. General Virtual Machines run on shared hardware which can go against specific security requirements. Azure Dedicated Hosts provides you with an assigned physical server within the Azure Datacenters, and these can be added to a host group to allow increased high availability.
Summary
This post has looked at services that provide security and governance resources like Key Vault and Azure Dedicated Hosts, which provide services to protect your applications and data. We also looked at services that monitor your environment for potential threats and attacks like Azure Sentinel and Azure Security Center.
—Matt Boyd