Azure Security Part 2: Understanding Azure Policies
What does Azure provide for Security?
Microsoft Azure has a wide range of services built into their cloud ecosystem. These services provide the ability to monitor resources, create and set policies, and identify and mitigate threats within not only the Azure infrastructure, but also to external resources for a consistent security posture across an organization. In the first post of a series of three articles on Azure Security, we focused on the services that make up the foundation of an organization’s security program. In this article, we will discuss how to govern the Azure environment with Policies.
What are Policies in Azure?
Challenges arise within a cloud environment when resources can be created that may affect, cost, security, or regulatory jurisdictions. Role-based access control (RBAC) and the principles of least privilege provide levels of restriction to users and groups within the environment as to what resources they can access or create, but they do not set parameters on where they can be created, the level of cost, or the security requirements. Azure policies are created, assigned, and utilized to govern the resources within your Azure subscription. Policies can be assigned using the built-in policies within Azure, of which there are hundreds, or custom policies can be created that may be necessary for your specific organizational needs. A list of these policies can be found here: https://docs.microsoft.com/en-us/azure/governance/policy/samples/built-in-policies.
Policies should be assigned at the beginning of building your environment in Azure but they can also be retroactively created, and existing resources can be audited against these policies. We will discuss this later in this article. Determining the policies to put in place should be based a business, security, and financial discussion. Governing your Azure environment for financial, business, and security will be discussed further in the following sections.
Financial Governance
We will begin our policy discussion with financial governance. Most of the financial and cost governance can be monitored and managed through the cost and billing services and Azure Advisor, with spending limits and controls being put in place for the subscription and resources. There are policies that can be put in place for controlling costs and performance compliance by assigning specific SKUs that are allowed within storage accounts, virtual machines (VMs), and VPN gateways. Assigning these policies, especially as they pertain to VMs, assist in controlling costs associated with deploying compute resources that are beyond what is necessary.
The screen shot below shows some of the built-in policies for financial governance.
Business Governance
The business and security governance areas are somewhat related. Both are focused on protecting the continued operation of the business. In terms of business governance, policies can be assigned to ensure that resources are created without violating any regulatory restrictions, such as GDPR. Azure has built-in policies for allowed locations that can be created for the entire subscription or can be assigned by resource group to segment jurisdiction as needed. These policies can be deployed within the Azure portal or through PowerShell using code available here: https://github.com/Azure/azure-policy/tree/master/samples/built-in-policy/allowed-locations.
The image below shows these policy definitions within the Azure portal.
Within the definitions, the parameters for data center locations are selected for where resources will be allowed to be created. If you are architecting the resource groups based on jurisdiction, the parameters can be assigned to only specific resource groups for segmentation. The ability to govern and audit where resources are created helps the business maintain compliance of where their data, backups, and sensitive information is held. In the event of an audit or legal seizure, proper jurisdictions can be verified and followed.
Within the built-in policies, there are over a dozen initiatives specific to the category of regulatory compliance. Initiatives are made up of a group of policies. This includes ISO27001, PCI, NIST, FedRAMP, HITRUST/HIPAA, UK NHS, and Canada PBMM. As you see in the below graphic, these are all initiatives that can be assigned to audit for these regulatory compliances. There are several policies within each of these audit initiatives as you can see in the second column.
If you select one of these initiatives, you can view the policies that are assigned. The NIST audit initiative itself has 798 policies that make up the audit. The ability to perform these audits are extremely helpful to a business since third party audits can be disruptive, time-consuming, and costly. It is important to note that not all policies are restricted to Azure resources. As we discussed in the part 1 of this blog series , Azure Monitor services can be used for Azure and external resources, and the information fed into Azure monitor and Azure Security Center. Azure Policies are gathering the information for these audits through the same activity and diagnostic logging. Enabling an organization to have a central policy that audits a hybrid architecture for regulatory compliance.
Security Governance
Securing and protecting resources within the environment is extremely important. Enabling compliance controls and policies can audit resources for specific regulatory requirements. If your organization is not required to adhere to any of the regulatory compliances, you may still find that auditing against one of the policies, NIST SP 800-53 for example, could provide you with a strong security baseline for controls within your environment. In addition, there are many built-in policies for security available. The list of policies can be found here: https://docs.microsoft.com/en-us/azure/governance/policy/samples/built-in-policies. These policies provide guidance for configuration policies of virtual machine guests, SQL databases, networking, monitoring, and Security Center. Built-in regulatory compliance initiatives can be reviewed on Microsoft Docs at this link: https://docs.microsoft.com/en-us/azure/governance/policy/samples/built-in-initiatives#regulatory-compliance.
Below is a sample list of policy definitions when searching ‘security’.
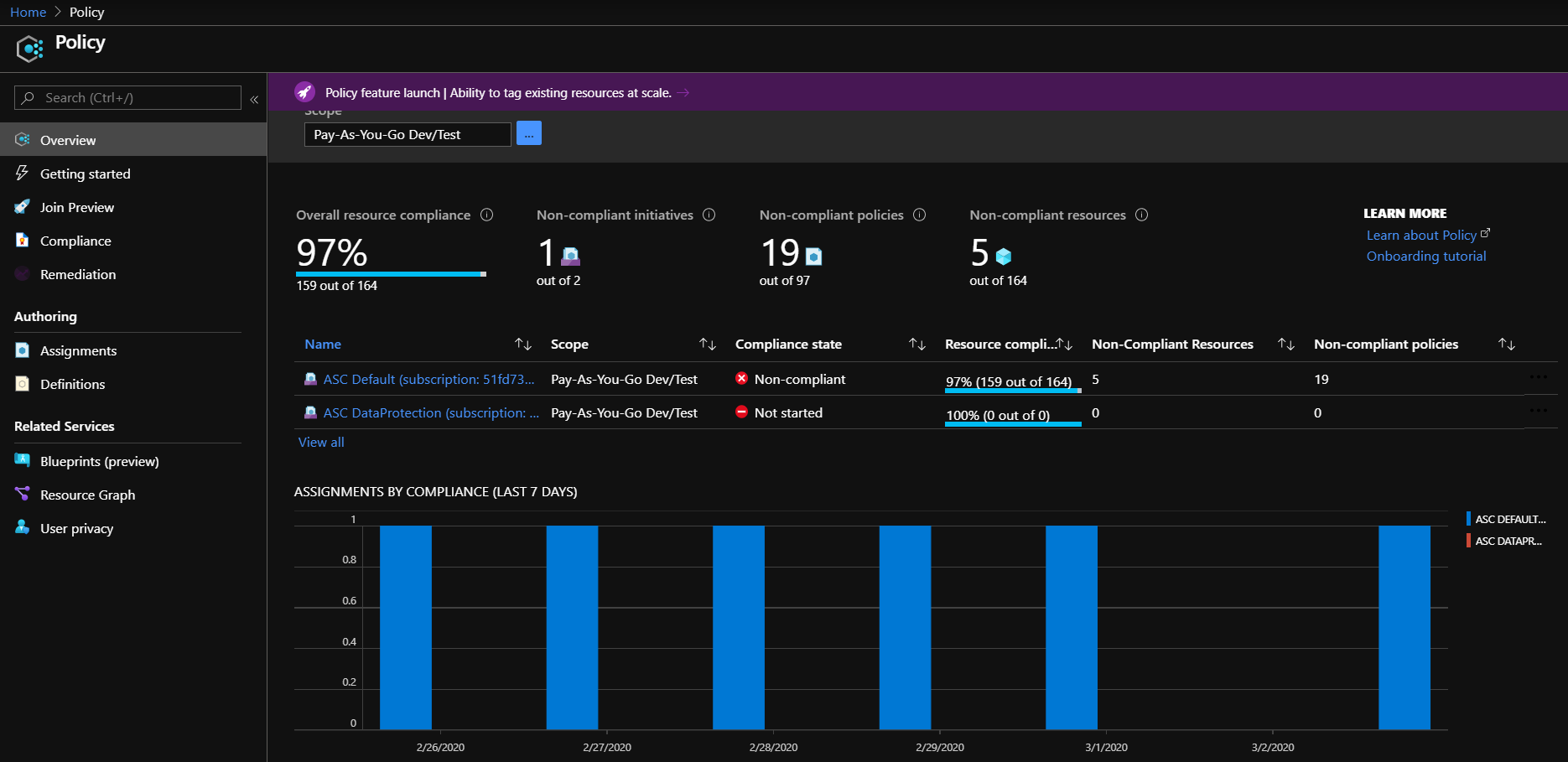
When searching on the term security, you will find some helpful initiatives, such as auditing VMs for security baseline settings and auditing VMs with insecure password settings. Both initiatives protect exposure of resources and allow an administrator to be proactive to potential vulnerabilities. The Policy service dashboard provides an overview of compliance.
If resources are non-compliant, they are identified and can be remediated directly from within the Policy service.
Azure Security Center
Compliance to policies and initiatives all feed into Azure Security Center. The first tile on the Security Center dashboard provides visibility into Regulatory Compliance (enabled with a Standard tier Security Center subscription) and a guide to assigning Azure Security Center policies within the recommendations tile (https://docs.microsoft.com/en-us/azure/security-center/tutorial-security-policy).
Within the Policy service definitions, there is a specific category for Security Center policies that can be assigned to allow data to be provided to the Security Center dashboard for an accurate Overall Secure Score for your subscription.
The below image shows some of the policies and initiatives that are listed when filtering the Categories to only show ‘Security Center’.
Azure Security Center is a central source for the overall security health of your organization’s environment, from a business and security governance perspective. From this central dashboard, there is the ability to drill down and access areas of policy non-compliance and remediate resources to maintain a strong security posture.
What’s Next?
As you build your Azure infrastructure and continue to add resources, it is important to determine the policies that your organization needs to adhere to for governance. Azure Security Center can help to track compliance to these policies. In our next blog, we will discuss security alerts and the use of runbooks.
Other Useful Resources
1. Azure Policy overview: https://docs.microsoft.com/en-us/azure/governance/policy/overview
2. Azure Security Center documentation: https://docs.microsoft.com/en-us/azure/security-center/
3. Microsoft Learn modules on Azure Policy: https://docs.microsoft.com/en-us/learn/browse/?products=azure&term=policy
4. Azure policy samples: https://docs.microsoft.com/en-us/azure/governance/policy/samples/
5. Built-in policies: https://docs.microsoft.com/en-us/azure/governance/policy/samples/built-in-policies
6. Built-in initiatives: https://docs.microsoft.com/en-us/azure/governance/policy/samples/built-in-initiatives
7. Tutorial on creating a custom policy definition: https://docs.microsoft.com/en-us/azure/governance/policy/tutorials/create-custom-policy-definition
—Dwayne Natwick
Let us know about your success! We love to empower our students and promote them. You can reach us on Twitter, LinkedIn or Facebook